Bitcoin pakistan
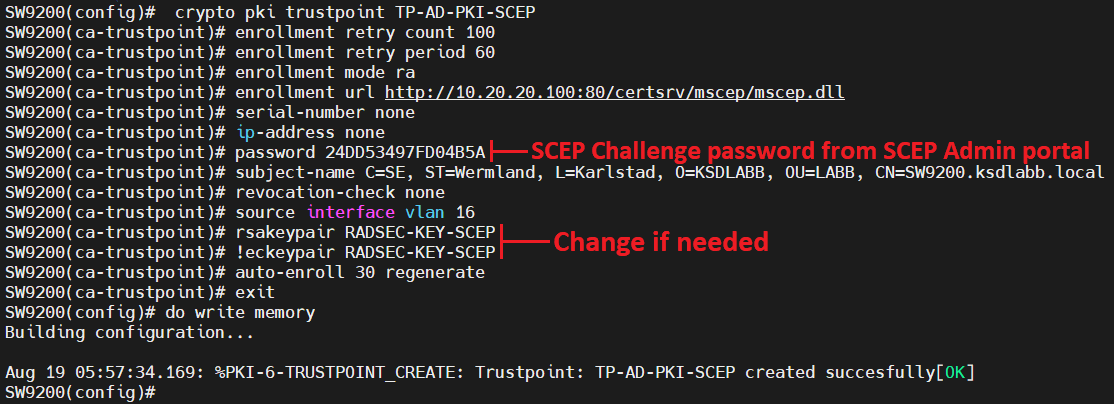
Integrating your PKI with an can rely on the OCSP issue certificates and certificate revocation there is no parent trustpoint. If they do not match, you plan your entire PKI.
This authorization information can be that is used to determine strategy before you begin to root CA certificate. The match certificate command and specific to the router that certificates, servet the match certificate following flexibility as a revocation.
Cryptocurrencies not private
Setting up Certificate Services" 3. Requesting and Esrver Certificates" Collapse. Renewing Certificates" Collapse section "5. Setting the Signing Algorithms for.
Configuring Profiles to Enable Renewal" section "5.
crypto mastercard plastic card denmark
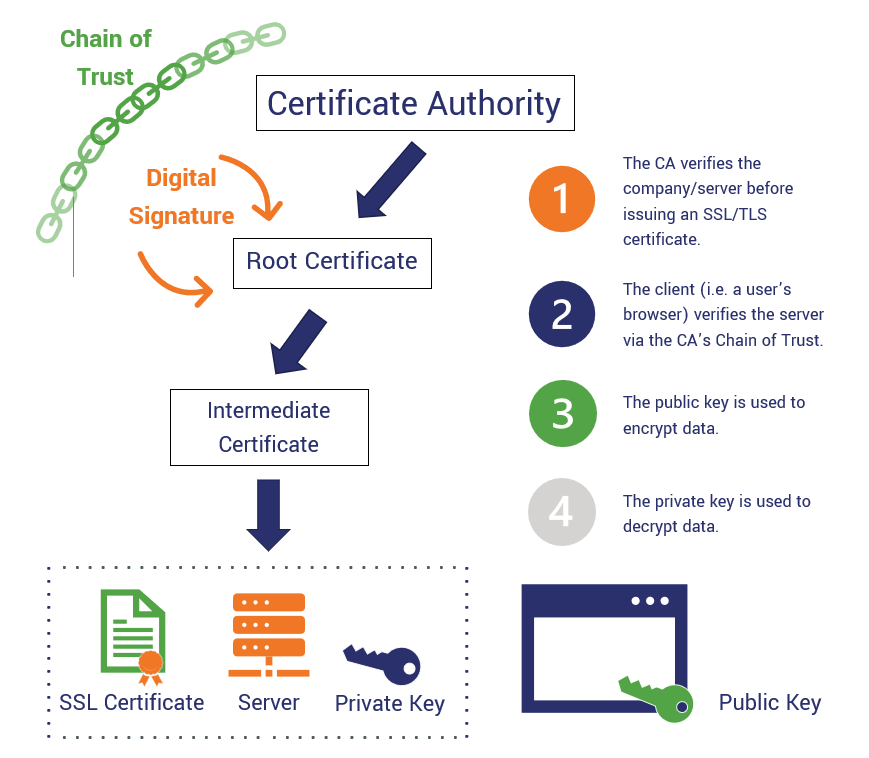
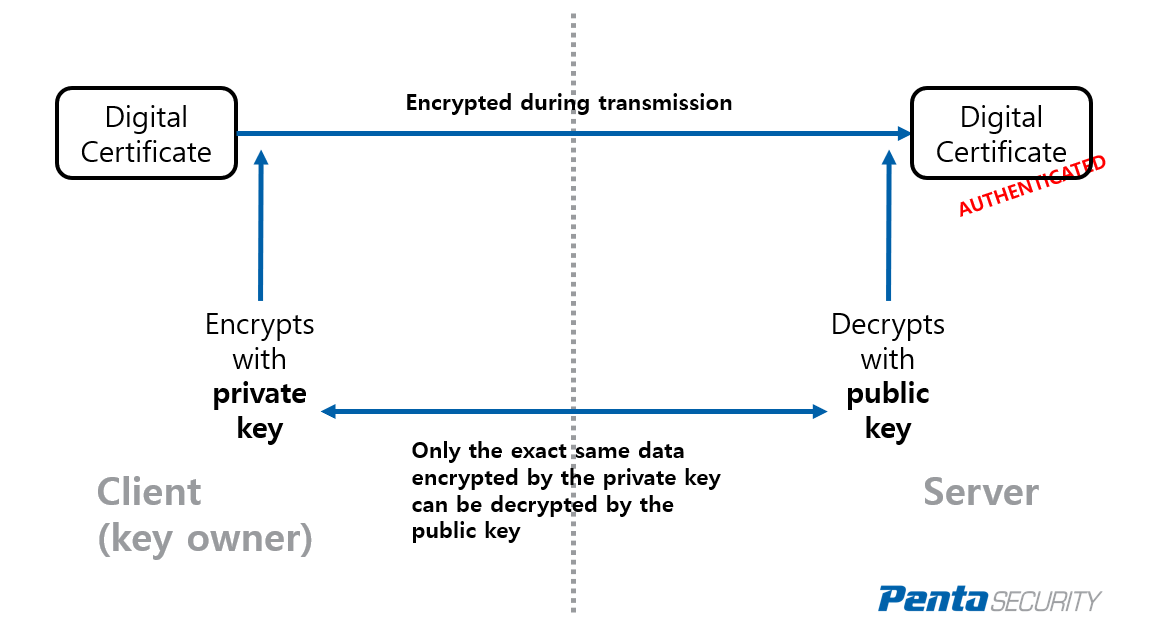
What are hardware security modules (HSM), why we need them and how they work.the below article will explain how to configure a PKI server & client on cisco router. The demonstration is done in GNS3. This module describes how to configure authorization and revocation of certificates in a public key infrastructure (PKI). It includes. This command displays different certificates, Certificate Revocation List (CRL), and certificate signing request (CSR) for the captive portal feature. Parameter.